Policy Development Kit
Accessing, using, and operating services for research in today’s world, as a rule, is inherently distributed, where users access resources outside their home organisations. In this complex environment, the question of trust for users, resource providers, and infrastructures, becomes paramount.
A set of policy documents is necessary to regulate and facilitate this trust. These policies outline the operational measures undertaken by the infrastructure to properly provide services. The policies principally cover security measures, user management and data protection.Policy may appear a daunting or overly complex task if you start on your research collaboration journey, but with eight simple steps you can quickly navigate the policy space and avoid the most common pitfalls.
What is the Policy Development Kit?
The Policy Development Kit (PDK)) offers policy templates to provide a head start for Research Infrastructures that want to deploy the AARC Blueprint Architecture. The policies are there to provide a starting point, so that Research Infrastructures do not have to re-invent the wheel!
Alongside the updated AARC Blueprint Architecture 2025 the PDK has been revised to make it easier for collaborations to adopt and integrate with the new trust framework. The PDK now is an on-line interactive resource that can be viewed on the AARC Wiki pages. It is intended to be used in two scenarios:
- The practical steps listed above are insufficient to address the policy needs of your research infrastructures due to size or complexity
- The practical steps above are not relevant as you have a more specific role such as the operator of an Authentication Source
The Policy Development Kit (PDK) version 2 identifies five main target audiences, functionally following the AARC BPA 2025 hierarchy and identifying:
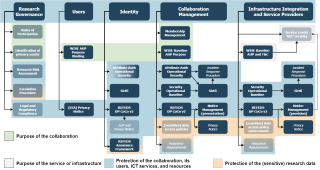
- ‘Research governance’ as a foundational area.
- ‘Users’ are (human) end-users who participate in a collaboration, are identified via
- ‘Authentication Sources’, i.e. external identity providers and the identity layer of the BPA, to be granted access by
- Collaboration Management’, to
- ‘Service and Infrastructure Providers’; in the BPA the infrastructure integration components, site-local integration components, and the actual service providers.
And be an early beneficiary of smoother trust and a new Snctfi, finding a provider of AAI platforms that already implements the key trust elements!
In addition to the templates, the AARC community over the years has also developed:
- Learn more about policies for the AARC Blueprint Architecture and videos from this course are also available on the AARC video playlist on YouTube GÉANT tv.
- A Training module on the GDPR Code of Conduct
- A Training Module on Policies for processing personal data
- The Policy guidelines offer more detailed advice on specific topics.
- The Snctfi framework- a ‘Scalable Negotiator for a Community Trust Framework in Federated Infrastructures’.
- The Sirtfi framework to identify trusted and operationally secure partners in a federated authentication and authorisation environment.
Policy Development Kit version 1 for larger and structured communities
| Document | Who should complete the template? | Audience | Description | Link |
|---|---|---|---|---|
| Top Level Infrastructure Policy | Infrastructure Management | All Infrastructure Participants (abides by) | This policy template defines the roles of actors in the Research Infrastructure and binds the policy set together | Google Doc |
| Incident Response Procedure | Infrastructure Management & Security Contact | Infrastructure Security Contact, Services (abides by) | This template procedure provides a step-by-step breakdown of actions to take following a security incident. | Google Doc |
| Membership Management Policy | Infrastructure Management | Research Community (abides by) | This policy template defines how Research Communities should manage their members, including registration and expiration. | Google Doc |
| Acceptable Authentication Assurance | Infrastructure Management | Research Community, Services (abide by) | This is a placeholder for the Infrastructure to determine rules for the acceptable assurance profiles of user credentials. | Google Doc |
| Risk Assessment | Infrastructure Management, Services & Security Contact | Infrastructure Management (completes) | This table can be used as a starting point for identifying whether a full Data Protection Impact Assessment is required. | Google Doc |
| Policy on the Processing of Personal Data | Infrastructure Management & Data Protection Contact | Research Community, Services (abide by) | This document defines the obligations on Infrastructure Participants when processing personal data. | Google Doc |
| Privacy Policy | Infrastructure Management (for general policy) & Services (for service specific policies) | Users (view) | This can be used to document the data collected and processed by the Infrastructure and its participants. Each service in the infrastructure, as well as the infrastructure itself, should complete the template. | Google Doc |
| Service Operations Security Policy | Infrastructure Management | Services (abide by) | This policy defines requirements for running a service within the Infrastructure. | Google Doc |
| Acceptable Use Policy | Infrastructure Management (for baseline) & Research Communities (for community specific restrictions) | Users (abide by) | This is a template for the acceptable use policy that users must accept to use the Research Infrastructure. It should be augmented by the Research Community. | Google Doc |


